
Real-Time Data Streams for AI Security Models
Modern threats online escalate in seconds, making traditional data analysis methods too slow for effective cybersecurity. Real-time data streaming enables AI models to detect and act on threats immediately, protecting users and brands from harm. Here's why this matters and how it works:
- Instant Threat Detection: AI processes live data to identify harmful behavior like harassment or predatory actions as they happen.
- Advanced Analysis: Beyond simple keyword detection, AI identifies patterns, context, and escalation to minimize false positives.
- US-Specific Challenges: Compliance with laws like CCPA and adapting to regional language nuances are key for effective implementation.
- Efficiency Gains: Real-time systems reduce workloads for security analysts by up to 37 times.
This article explores how real-time AI systems safeguard messaging platforms, protect athletes and creators, and balance speed with privacy regulations.
AI Security: Protecting AI with Automated Real-Time Threat Detection
Core Requirements for Real-Time Model Updates
Creating real-time AI security models isn't just about having smart algorithms - it’s about building an entire system capable of handling massive data streams and making lightning-fast decisions. To achieve this, you need three critical components working together: scalable infrastructure, precise feature engineering, and systems that can learn and adapt on the fly.
Building Scalable and High-Speed Infrastructure
The backbone of any real-time AI security system is its infrastructure. It needs to process millions of events every second without breaking a sweat. Tools like Apache Kafka are often used for high-throughput data ingestion, ensuring a steady flow of messages and user interactions. As data volumes grow, the system must scale horizontally, adding extra power without compromising speed.
Distributed frameworks like Apache Flink or Spark Streaming transform raw data into actionable insights. And when it comes to detecting harmful content or threats, speed is non-negotiable - every millisecond counts. Sub-second response times can mean the difference between stopping a harmful message and letting it slip through.
Low-latency storage solutions are another must. These provide instant access to critical data, like threat intelligence and user behavior patterns. Traditional databases that take seconds to respond just won’t cut it in a real-time environment.
Data quality is equally crucial. Issues like missing fields, duplicates, or inconsistent formats can throw off the entire system, leading to missed threats or false alarms. To counter this, organizations need tools for schema validation, deduplication, and real-time monitoring to catch and fix problems before they affect security decisions.
For US-based companies, there’s an added layer of complexity: compliance. Infrastructure must meet data residency requirements, ensuring sensitive information stays within US borders, all while maintaining the speed and scale needed for effective threat detection.
Feature Engineering for Security Models
Effective threat detection goes beyond basic keyword matching. Modern AI models need to understand context. For instance, a single word might seem harmless, but its meaning can shift dramatically depending on the conversation. This is especially important for spotting sophisticated threats that rely on subtlety.
Linguistic features are a key part of this process. Tools like sentiment analysis and toxicity scoring help identify escalating behavior. Models designed for US-based contexts also need to account for regional slang, references, and context-specific threats, especially in industries like sports or influencer management.
Behavioral patterns add another layer of protection. Tracking message frequency, timing, and escalation helps identify coordinated harassment campaigns or predatory behavior that unfolds over time. For example, grooming cases often start with private direct messages and escalate gradually - patterns that AI needs to detect.
Supporting multiple languages is also essential. Many online communities are linguistically diverse, with users frequently switching between languages or mixing them in a single conversation. Models must account for this to catch nuanced threats without raising unnecessary alarms.
Finally, smart filtering systems that understand context are crucial. By moving beyond simple keyword-based detection, these systems can reduce false positives, ensuring that regular conversations aren’t flagged while real threats are caught promptly.
Online Learning and Incremental Updates
Threats evolve quickly, and AI models need to keep up. Traditional models that require full retraining can’t adapt fast enough. That’s where online learning comes in. These algorithms update incrementally as new data comes in, allowing the system to evolve without starting over from scratch.
This adaptability is critical in security, where new threat patterns emerge constantly. Online learning improves detection accuracy while reducing false positives, ensuring the system stays effective over time.
Feedback loops play a big role here. Whether it’s a security analyst or an automated system validating a model’s output, that feedback helps refine future predictions. This creates a cycle of continuous improvement, making the system smarter and more reliable with every iteration.
The infrastructure supporting online learning must handle real-time updates without disrupting ongoing operations. Automated triggers can detect when model performance dips or when new threats arise, prompting updates or flagging issues for human intervention.
For organizations managing sensitive content, staying ahead of rapidly evolving threats is essential. Continuous learning systems enable AI to adapt quickly, ensuring it can counteract new tactics designed to bypass detection.
AI-Powered Threat Detection in Messaging Platforms
Messaging platforms have become prime targets for online threats. Whether it’s harassment campaigns aimed at NFL players or predatory behavior infiltrating youth sports communities, the stakes have never been higher for effective threat detection. Modern AI systems face the challenge of processing millions of messages in real time, all while deciphering context, understanding cultural nuances, and identifying subtle patterns that differentiate genuine threats from harmless conversations. To meet these demands, diverse and adaptable AI models are essential. Let’s break down how these systems work.
Key Machine Learning Models for Moderation
Keeping messaging platforms secure depends heavily on advanced AI models working in unison. Deep learning architectures, particularly transformer-based models like BERT, are incredibly effective at understanding natural language context. These models excel at spotting nuanced harassment patterns that traditional keyword filters often miss.
Decision trees add another layer of sophistication by analyzing behavioral patterns and user histories. For instance, if a user sends a series of increasingly aggressive messages over a few days, decision trees can identify this escalation as a potential risk. Meanwhile, anomaly detection algorithms play a crucial role in spotting unusual messaging behaviors, such as coordinated harassment campaigns or activity from bot networks.
Together, these models form a comprehensive risk-scoring system. A single offensive word might not raise alarms, but when combined with escalating behavior or abnormal account activity, the risk score increases significantly. This layered approach boosts accuracy, reduces false positives, and addresses the complexities of moderating a global audience.
Multilingual Comment Moderation and DM Threat Detection
For US sports leagues and influencer communities, the challenges of moderating a global, multilingual audience are immense. An NBA player, for example, might receive threatening messages in Spanish, Mandarin, or Arabic. Similarly, MLS athletes often face harassment in multiple languages during international events. Relying on English-only moderation leaves significant blind spots.
Thankfully, advanced AI systems now support over 40 languages, thanks to multilingual natural language processing models trained on diverse datasets. These models go beyond simple translation - they interpret cultural contexts, regional slang, and other nuances that could signal a threat. Transfer learning further refines these base models, tailoring them for specific areas like sports or entertainment.
As online threats evolve, AI must constantly adapt to new tactics and emerging terminology to stay effective.
Guardii's Role in Ensuring Safety
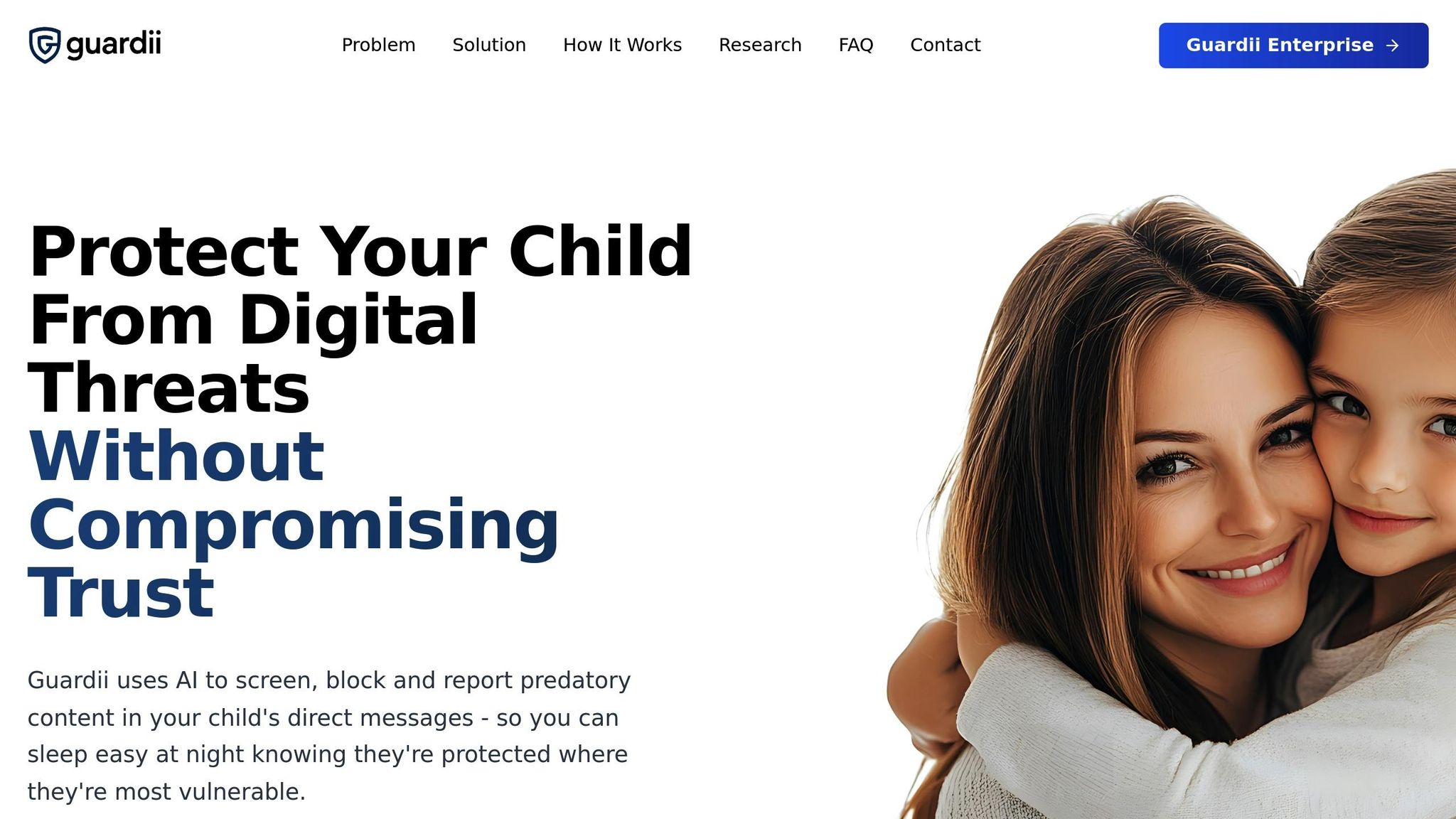
Guardii.ai provides a real-world example of how AI-powered protection is transforming safety for US-based organizations. The platform moderates Instagram comments and direct messages across more than 40 languages, offering protection for sports teams, athletes, influencers, and families through advanced threat detection algorithms.
Guardii’s technology goes far beyond simple keyword matching. It analyzes context, behavioral trends, and escalation patterns to distinguish between enthusiastic fan interactions and genuine threats. Cyber safety expert Susan McLean emphasizes the importance of guidance in today’s digital world:
"Kids are tech-savvy, but not threat-savvy. They need guidance, not just gadgets."
When concerning content is flagged, Guardii automatically quarantines it while preserving evidence for potential legal action - a critical feature, given that only 10–20% of online predation cases are reported to authorities. High-risk content, such as explicit threats or sexual harassment, is prioritized for immediate human review, while lower-priority cases are handled automatically.
For legal and brand safety teams in the US, Guardii generates detailed evidence packs and audit logs that comply with American legal standards. These reports include timestamps, redacted user identifiers, and contextual metadata to aid investigations or legal proceedings. John Shehan from the National Center for Missing & Exploited Children highlights the urgency of this issue:
"Predators don't need to be in the same room. The internet brings them right into a child's bedroom."
Proper evidence collection is crucial for protecting victims and ensuring justice.
Guardii’s Meta-compliant design ensures that automated actions, such as hiding comments or blocking accounts, align with platform policies. This reduces the risk of appeals or policy violations - an especially critical factor for high-profile athletes and influencers who are constantly in the public eye.
Beyond individual safety, Guardii’s robust moderation also supports brand reputation. By maintaining a clean, safe environment while preserving genuine fan interactions, the platform helps protect both personal and corporate reputations, ensuring long-term trust and engagement.
sbb-itb-47c24b3
Integrating Real-Time Data Streams for Model Updates
To keep AI security models effective, they need to process real-time data streams efficiently, turning raw information into actionable insights. This process allows the models to adapt to new threats and shifting user behaviors on the fly. Building on earlier discussions about scalable systems and dynamic learning, let’s dive into how data streams are ingested, refined, and fed back into models in real time.
Stream Ingestion and Preprocessing
Platforms like Apache Kafka play a key role in managing high-speed, high-volume data flows. These systems allow organizations to handle millions of events per second without slowing down or losing performance.
To ensure data quality during ingestion, strict schema contracts are essential. These contracts define the structure of incoming data - field names, data types, and acceptable value ranges. If data formats are inconsistent, it can lead to corrupted model predictions, resulting in false alarms or missed threats.
The preprocessing pipeline tackles several crucial tasks simultaneously:
- Deduplication: Filters out repeated messages that could distort analysis.
- Normalization: Scales numerical data to consistent ranges, making comparisons over time more reliable.
- Standardization: Ensures text data follows uniform rules, such as converting to lowercase, removing special characters, and handling various encoding formats.
For multilingual systems, preprocessing becomes even more intricate. Text must be tokenized with attention to language-specific details, including regional slang or cultural nuances that might signal a threat. For instance, natural language processing models can detect harmful content in languages like Spanish, Mandarin, or Arabic, but only if the preprocessing pipeline correctly handles linguistic and encoding challenges.
Missing data is another critical issue. Gaps in logs or metadata might not just be errors - they could indicate a security event. For example, the sudden absence of activity logs might point to a system breach, or missing user information could suggest tampering with accounts.
Model Tuning for Security Applications
Real-time security systems need models that make split-second decisions without compromising accuracy. Several optimization techniques help meet this challenge:
- Model pruning: Removes unnecessary parameters, often shrinking the model by 50-90% while keeping accuracy intact.
- Quantization: Reduces parameter precision (e.g., from 32-bit to 8-bit), speeding up inference by 3-4 times with minimal accuracy trade-offs.
- Knowledge distillation: Transfers the knowledge of large, complex models into smaller, faster ones, enabling lightweight models to detect threats efficiently.
Once data is cleaned and standardized, these techniques ensure the model can detect threats quickly and accurately. However, optimization requires rigorous testing, including scenarios designed to trick the system. A/B testing in live environments helps confirm that these optimized models maintain their protective capabilities while delivering the speed improvements needed for real-time applications.
Feedback Loops and Continuous Improvement
Real-time updates are crucial for AI security systems to stay effective. Continuous feedback mechanisms allow these systems to learn from their environment, improving their performance over time.
Key metrics - like detection latency, false positive/negative rates, and data throughput - must be monitored in real time. If these metrics fall outside acceptable ranges, automated systems can trigger retraining or alert human operators to investigate. For organizations in the U.S., this monitoring must align with privacy laws like the California Consumer Privacy Act (CCPA).
Human-in-the-loop validation plays a pivotal role in refining high-stakes decisions. When AI models flag potential threats, human reviewers confirm or reject these findings. This process not only ensures accuracy in critical moments but also generates valuable training data for future model updates. This step is especially important for content moderation, where understanding context and applying subjective judgment are often necessary.
Tracking the outcomes of incidents helps connect model predictions to their real-world impact. Successfully mitigating threats reinforces the model’s decision-making, while missed threats highlight areas for improvement, such as adding more training data or adjusting the model’s architecture.
Incremental learning allows models to adapt steadily to new threats without destabilizing the system. Updating too frequently can make the system erratic, while infrequent updates leave it vulnerable to emerging risks.
Maintaining audit trails is also essential. Detailed records of model updates, training data, and performance changes are critical for regulatory compliance and forensic investigations. For U.S.-based organizations, this documentation is not just a best practice - it’s often a legal requirement.
For entities like sports teams, influencers, or content creators, feedback loops must also account for unique challenges. For example, fan enthusiasm might be misinterpreted as threatening behavior, while actual threats could be disguised as routine interactions. Over time, continuous learning helps models better distinguish between these scenarios, reducing false positives while still ensuring robust protection against genuine risks.
Evidence and Audit Workflows for Safety and Brand Teams
When AI security models detect threats in real time, the next step is turning that raw data into actionable intelligence for safety, legal, and brand teams. This involves creating secure documentation workflows that not only translate threat data into meaningful insights but also ensure the legal chain-of-custody. These workflows seamlessly connect with real-time data processing, creating a fully integrated security approach.
Generating Evidence Packs and Audit Logs
Evidence packs are carefully assembled collections of incident data that document the entire lifecycle of a threat - from detection to resolution. These packs include key details like the original content, user metadata, timestamps formatted for U.S. standards, moderation actions taken, and contextual screenshots to provide a comprehensive view of the incident.
The process of generating these evidence packs is automated and happens in real time, capturing every interaction within milliseconds of a threat being identified. This ensures that no crucial data is lost.
Audit logs serve as a chronological record, tracking every step of an incident. They document everything from the initial detection by AI algorithms to the final decisions made during human review. For U.S.-based organizations, these logs include time zone details and are protected through encryption and strict access controls to maintain data integrity.
To further ensure legal admissibility, chain-of-custody metadata is included. This metadata tracks who accessed the data, when changes were made, and other critical details, making the evidence reliable for legal proceedings.
Preserving Brand and Sponsor Reputation
For high-profile events, the ability to rapidly generate evidence and provide transparent reporting is key to managing reputational risks.
Take, for example, an athlete receiving threatening messages during a tournament. The AI system detects and quarantines the threats, documents the incident, and immediately notifies the brand management team. The resulting evidence pack not only contains the threatening messages but also highlights the swift actions taken, showcasing proactive measures to protect the individual.
For sponsors, clear communication backed by thorough documentation is essential. Quick access to evidence packs detailing incidents and responses helps mitigate bad publicity and maintain sponsor relationships. At the same time, features like auto-hide functionality ensure that harmful content is removed from public view almost instantly, while preserving it in a secure quarantine for evidence purposes. This strikes a balance between immediate action and accurate record-keeping.
Post-incident reports offer sponsors and brand teams valuable insights into threat trends, response times, and the effectiveness of protective measures. These reports, derived from audit logs and evidence packs, support decisions on future security investments and highlight ongoing efforts to ensure safety.
Building Effective Watchlists and Reporting Workflows
Real-time model updates are complemented by automated watchlists and reporting workflows, enabling a shift from reactive to proactive security. AI-driven watchlists flag users who repeatedly violate guidelines or escalate threatening behavior, allowing for immediate action when these individuals target new victims.
These watchlists are dynamic, relying on continuous real-time behavioral analysis. As a user's behavior worsens - moving from toxic comments to direct threats - the system adjusts their risk score and response protocols accordingly. This ensures that high-risk individuals receive prompt attention while minimizing false alarms for lower-priority cases.
Streamlined reporting workflows connect evidence generation directly to law enforcement and regulatory requirements. Efficient reporting is crucial for timely intervention by law enforcement agencies.
"The research clearly shows that preventative measures are critical. By the time law enforcement gets involved, the damage has often already been done."
- Guardii's 2024 Child Safety Report
Integration with case management systems allows security teams to track incidents from start to finish. Features like automated evidence pack creation and one-click exports reduce manual labor while maintaining consistent documentation. This standardized approach is vital for coordinating multiple incidents with law enforcement.
Cross-team collaboration is also enhanced through automated workflows. Alerts notify all relevant stakeholders when serious incidents occur, with role-based access ensuring that each team gets the information they need - legal teams receive full evidence packs with chain-of-custody details, while brand teams get sanitized summaries focused on reputation management and response timelines.
Automation also helps with regulatory compliance. For U.S.-based organizations, these systems can generate reports that meet state and federal requirements, covering everything from data retention rules to privacy protections and incident notification timelines. This reduces the burden of compliance while ensuring adherence to legal standards.
Regular reviews of watchlists and workflow audits keep the system effective. Monthly analyses of repeat offender patterns, false positives, and response times allow for continuous improvement. This ensures that detection algorithms and human response processes adapt to evolving threats, maintaining both legal and operational effectiveness.
These workflows tie back into the broader goal of integrating real-time data to continually refine AI security models and enhance overall protection efforts.
Best Practices and Future Directions
The pace of development in real-time AI security models is accelerating, fueled by increasingly sophisticated threats and the demand for rapid response capabilities. These evolving practices build on the scalable systems already in place, from stream ingestion and model adjustments to feedback mechanisms and evidence workflows.
Key Takeaways for US-Based Organizations
For organizations in the United States, maintaining high-quality data and strong governance is critical to effective real-time AI security. Without reliable data, even the most advanced models can falter - leading to false positives that overwhelm security teams or false negatives that let threats slip through. To address this, companies should implement robust data governance frameworks. These should include encryption, role-based access controls, and thorough audit logging to meet regulatory standards.
Real-time streaming architectures have proven their value, significantly reducing response times. When implemented correctly, these systems can cut response times from hours to minutes, reduce false positives by 60%, and decrease analyst workloads by a factor of 37.
Context-aware detection is another game-changer. This approach goes beyond simple keyword matching to analyze communication nuances, making it possible to identify genuine threats while reducing the burden on moderators. By examining conversation patterns and behavioral escalations, context-aware systems deliver greater accuracy and efficiency.
Automated feedback loops are key to keeping AI models sharp. These systems allow continuous learning, enabling AI to adapt to new attack strategies and behavioral trends. Combined with evidence-driven workflows, they not only strengthen detection but also support legal processes and compliance with regulations.
As organizations adopt these practices, they must also prepare for emerging challenges and opportunities.
Future Challenges and Opportunities
With strong foundational systems in place, the next big challenge lies in managing multilingual and multicultural content moderation. As platforms expand globally, AI models need to handle diverse languages and cultural nuances while maintaining consistent safety standards. Tools like Guardii are already tackling this by moderating comments and direct messages in over 40 languages, offering protection for a wide range of users.
Privacy regulations will also play a major role in shaping AI security strategies. Organizations will need to strike a balance between effective threat detection and user privacy by embedding privacy-by-design principles into their systems.
The rise of AI copilots and automated investigation tools presents a major opportunity. These tools can streamline threat investigations by gathering evidence, analyzing risks, and presenting findings in a clear, concise format. This allows security teams to focus their attention on complex cases that require human expertise.
As threats become more complex, adaptive protection mechanisms will be crucial. Future AI security systems must dynamically adjust their monitoring and response strategies based on risk levels, user behavior, and emerging threat intelligence. This ensures resources are used effectively while maintaining strong defenses.
Finally, cross-platform threat intelligence sharing offers a promising avenue for enhanced security. By pooling threat data from multiple sources, organizations can gain a more comprehensive view of the threat landscape, enabling better predictions and faster responses.
The organizations that combine technical precision with the ability to adapt quickly to new challenges will be the ones to thrive in this ever-evolving security environment.
FAQs
How do real-time AI security models balance fast threat detection with compliance to privacy laws like the CCPA?
Real-time AI security models are built to handle data swiftly while staying compliant with strict privacy laws like the California Consumer Privacy Act (CCPA). They achieve this balance by using methods such as data anonymization, limiting how long data is stored, and employing secure processing practices to safeguard user privacy.
These models prioritize speed in threat detection by focusing on behavior patterns and metadata rather than collecting or exposing sensitive personal details. This approach enables them to spot potential risks - like harmful messages or harassment - without crossing legal or ethical boundaries. By working within these limits, AI systems provide strong protection while upholding privacy standards.
How do context-aware systems differ from traditional keyword detection in AI security models?
Traditional keyword detection works by matching specific words or phrases to flag potential threats. While this method can work well in straightforward situations, it often falls short when dealing with more subtle elements like slang, sarcasm, or contextual meanings. As a result, it can lead to a higher rate of false positives or negatives.
In contrast, context-aware systems use real-time data streams and advanced AI technologies like natural language processing (NLP) and machine learning. These systems go beyond just words - they analyze the overall context of a message, including its tone, intent, and how words relate to one another. This approach allows for more precise threat detection, especially in complex, multilingual settings or when facing evolving security challenges.
How does Guardii improve threat detection and moderation across multiple languages and cultural contexts?
Guardii's AI models are built to handle content analysis in over 40 languages, making them highly effective for moderating social media interactions such as comments and direct messages. These models go beyond simple translation, factoring in subtle linguistic differences and cultural nuances to detect and address toxic behavior, threats, and harassment with precision.
When suspicious content is detected, it’s flagged or quarantined for further review. Harmful material can be auto-hidden or forwarded to the appropriate teams for action. This multilingual, context-aware system plays a vital role in creating a safer online space for athletes, influencers, journalists, and families, promoting a more secure and positive digital environment.